Close the gaps before attackers find them
AllyRight AI pinpoints vulnerabilities and helps patch them fast.
400 Million+
Pages Audited
80 Billion+
Issues Detected
That's a lot of broken code — and a lot of users who never even noticed, thanks to AllyRight.
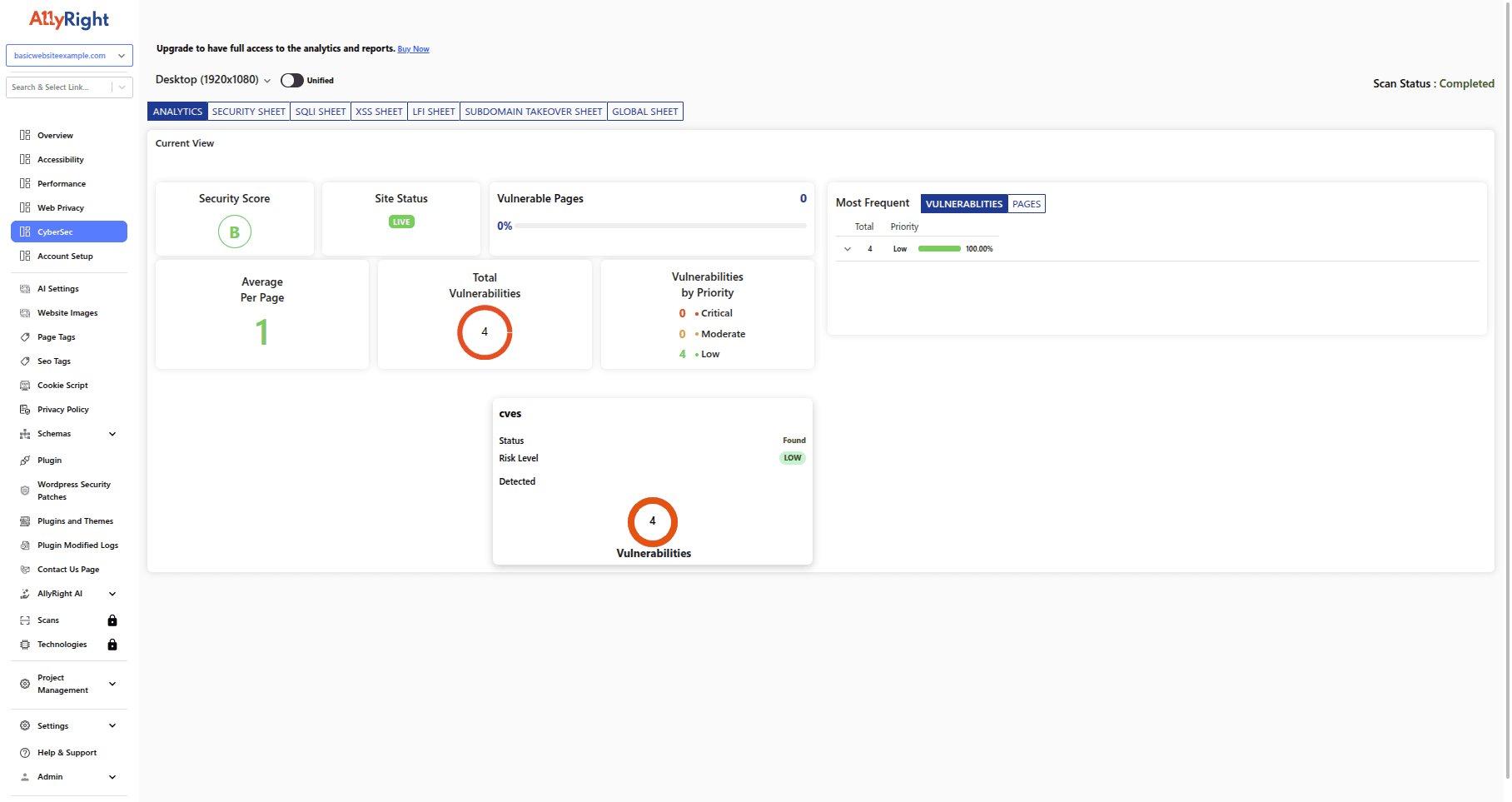
Vulnerability scanning that keeps attackers off the court
Security should feel proactive, not reactive. AllyRight AI continuously scans your site for vulnerabilities, outdated dependencies, and missing security headers, then delivers safe fix recommendations before attackers even notice. Less firefighting, fewer 2 a.m. alerts — just a stronger, more resilient site your team can trust.
Security — Risk of Non-Compliance
Website security isn't optional — one missed patch can cost millions. Hackers exploit outdated code, weak headers, and hidden flaws before you even notice.
Costly breaches
Vulnerabilities invite data theft, ransomware, and breaches. Each incident brings expensive recovery bills and possible lawsuits.
Government oversight
Failing a security audit can trigger mandatory monitoring, restrictions, or loss of contracts.
Downtime losses
Attacks don't just steal data — they knock services offline. Every hour down means lost revenue and frustrated customers.
Compliance failures
Missing security headers, outdated dependencies, and weak configurations can fail both internal and external audits.
Reputation collapse
Customers rarely forgive breaches. A single exploit can erode trust and damage your brand permanently.
How AllyRight AI Works
Lightning-fast crawl
AllyRight scans up to 15,000 pages per second, capturing every asset and script. From outdated headers to hidden flaws, nothing is missed.
Deep multi-module analysis
One platform integrates security scanning with accessibility, privacy, SEO, and performance checks. Teams get complete visibility in one place.
Actionable reports
AllyRight prioritizes vulnerabilities by exploitability and risk. Instead of overwhelming lists, you get clear, ranked reports.
Safe, code-level remediation
Our AI applies safe changes directly to source code, with pull requests for review. Critical issues are patched faster, without sacrificing control.
Continuous monitoring
Security isn't one-and-done. AllyRight runs recurring scans, alerting you to regressions and new threats so your defense never slips.
Security Features
Website security isn't optional — it's the foundation of user trust and business continuity. AllyRight automates scans, applies safe fixes, and guides your team through remediation.
Autonomous Remediation for Web Vulnerabilities
Automated Security Crawler: Our crawler scans every rendered page, asset, and script to uncover vulnerabilities in real environments. Dynamic testing reveals risks static scans miss, giving you a true picture of your attack surface.
AI-Powered Auto-Fixes for Security: AllyRight AI suggests fixes for weak headers, insecure configurations, and outdated CMS settings. Changes can be staged or pushed as pull requests, reducing patch timelines from weeks to hours.
Configurable Autonomy for Security: Teams choose which fixes run automatically and which need human approval. Low-risk updates may be applied instantly, while sensitive changes wait for sign-off. This delivers both agility and safety.
Element Location Identification: Every vulnerability comes with DOM selectors, file paths, and patch-ready diffs. Developers jump straight to the issue instead of wasting hours searching.
Ongoing Security Scans: Continuous monitoring ensures new vulnerabilities are caught as your site evolves. Dashboards and alerts keep your team ahead of threats.
Website Security Scanning
TLS/SSL Certificate Validation: Certificates are checked for strength, expiration, and configuration. Weak setups are flagged early, preventing browser warnings and man-in-the-middle risks.
CORS Policy Validation: Cross-origin resource sharing settings are validated to prevent data leaks. AllyRight highlights misconfigurations and provides practical fix recommendations.
CDN Security Configuration: Content delivery networks are reviewed for outdated, exposed, or insecure settings. This prevents CDN missteps from becoming attack vectors.
Vulnerability Detection Tools
DDoS Attack Pattern Detection: AllyRight monitors for unusual traffic spikes that may indicate denial-of-service attempts. Early alerts help contain threats before they escalate.
SQL Injection Detection: Databases are scanned for injection risks with remediation steps tailored to your stack. Closing these gaps prevents one of the most common attack types.
Cross-Site Scripting (XSS) Detection: Input points are tested for XSS vulnerabilities that could hijack sessions or data. Detailed reports show exactly where to patch.
Local File Inclusion (LFI) Scanning: Checks identify weaknesses that allow unauthorized file access. Clear prevention techniques are included to reduce risk.
Subdomain Takeover Monitoring: AllyRight detects orphaned or vulnerable subdomains that attackers could hijack. Reports explain risks and mitigation strategies.
Ready to Fortify Your Security?
Join organizations protecting their users and reputation with proactive vulnerability management.